Centered on recent threat action, privileged accounts, not corporate knowledge, could possibly be the most useful things within just organization networks.
Various classes at Gartner’s 2020 Stability & Danger Management Summit this 7 days concentrated on the great importance of privileged obtain administration to cybersecurity, and how threat actors have increasingly concentrated attempts to hijack or get hold of privileged accounts. In a Monday session titled “Outlook for Id and Entry Management,” Gartner senior analysis director David Mahdi reviewed what a prosperous id and obtain administration (IAM) software appears to be like like in 2020, as properly as the increasing great importance of privileged obtain administration and other matters.
Mahdi’s presentation reviewed the concept of pace compared to accuracy in a crisis scenario when right away responding to a crisis, pace of reaction to “cease the bleeding” is more significant than accuracy at the minute. When the crisis moves from “respond” to “recover” and “renew,” then it truly is significant to start off contemplating about how a corporation can get back again up on its feet and how it can make a more efficient cybersecurity basis for the potential.
Great IAM, Mahdi explained, is like a good pit crew that balances the great importance of having a racer back again on the track swiftly (pace) with the great importance of building certain a wheel isn’t going to occur off mid-race (accuracy). To give an business “pace for survival,” Mahdi recommended prioritizing the enablement of protected distant obtain, federated SSO and multifactor authentication (MFA) and both equally quick and “good more than enough” IAM and consumer IAM or CIAM. And then to keep accuracy, an business really should concentration on account takeover defense, fraud detection, privileged obtain administration and converged, less expensive SaaS-delivered IAM.
“If you are not applying privileged obtain administration tools, engineering, folks and process wherever you have this embedded in the fabric of your business, now’s the time to do it. Why? Terrible fellas are likely immediately after privileged end users. Privileged end users have obtain to your delicate knowledge, and they have obtain to the keys to your kingdom. And that’s what you genuinely want to protect,” Mahdi explained.
In yet another Monday presentation that touched on privileged obtain administration, titled “Deconstructing the Twitter Attack — The Function of Privileged Accounts,” CyberArk principal remedies engineer Matt Tarr reviewed the social engineering assault versus Twitter from this summer time that resulted in approximately $121,000 in bitcoin becoming ripped off from end users. He argued “basic consumer protection instruction” and privileged obtain administration could have slowed or stopped the activities from unfolding.
“This assault highlights the risks of unsecured privileged obtain. It really should remind us how swiftly any credential or id can grow to be privileged beneath specified circumstances. If not thoroughly secured, external attackers and malicious insiders alike can use them to unlock critical assets, whether or not that’s with a domain admin or a simple aid account that can make improvements with a Twitter profile,” he explained.
Tarr mentioned the infamous assault was not automatically sophisticated possibly.
“Originally considered to be the perform of seasoned country-condition attackers, it now appears the social engineering-initiated assault was performed by a comparatively unsophisticated group of hackers motivated by fiscal achieve and/or neat monitor names,” he explained. “Yup, monitor names.”
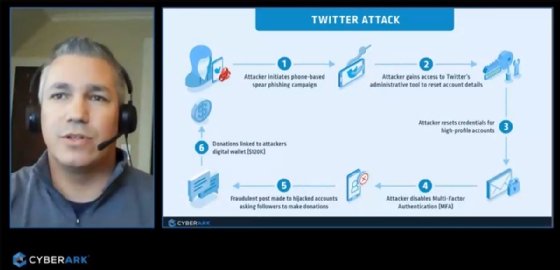
Tarr explained the breach demonstrated that it was simpler for the attackers to break into Twitter alone than to break into a Twitter account with MFA enabled. The assault commenced with a cellphone-centered spear phishing or vishing marketing campaign that targeted precise Twitter personnel. Once the attackers received personnel qualifications, they acquired obtain to Twitter’s administrative tools and disabled the MFA defense on quite a few significant-profile accounts. Due to the fact Twitter lacked appropriate protection controls close to individuals admin tools, the attackers have been ready to abuse them when remaining beneath the radar. Basically, Twitter experienced much better account defense for end users than it did for its own directors, he explained.
Tarr reviewed mitigations versus these kinds of social engineering attacks that may perhaps happen in the potential. He recommended cybersecurity recognition instruction for personnel, applying sturdy passwords, prioritizing privileged obtain administration and developing a conditional policy that mandates multifactor authentication.
In a Tuesday session, titled “Stability Leader’s Guide to Privileged Entry Management,” Gartner analysis director Felix Gaehtgens explained privileged obtain administration is a vital part of any protection software due to the fact of the increasingly huge scope of IT environments, privileged end users, administrative tools, and IAM knowledge this sort of as passwords, encryption keys and certificates. Gaehtgens recommended organizations apply rigorous controls on privileged obtain this sort of as restricting the complete amount of personal privileged accounts, developing more shared accounts and minimizing the situations and durations throughout which privileged obtain is granted.






